MAC stands for Media Access Control. It is a unique identifier assigned to a network interface controller (NIC) for Ethernet or Wi-Fi. MAC addresses are 12-digit hexadecimal numbers that are burned into the NIC’s hardware.
MAC addresses are used by network devices to identify each other and to control access to the network. When a device sends a packet of data over the network, it includes its MAC address in the header of the packet. The receiving device then uses the sender’s MAC address to route the packet to the correct destination.
- Introduction
- Role of MAC Addresses in Data Transmission
- Unicast, Broadcast, and Multicast MAC Addresses
- MAC Address vs. IP Address
- MAC Address Spoofing and Security
- Changing MAC Addresses and Privacy Concerns
- MAC Filtering and Network Access Control
- MAC Addresses in Wireless Networks
- Conclusion
- FAQs
Introduction to MAC
Understanding MAC Addresses: Identifying Devices in Networks At its core, a MAC address is a unique identifier assigned to every network interface controller (NIC) in a device. Much like a physical address for a house, a MAC address serves as a virtual address for devices within a network. Whether it’s a computer, smartphone, printer, or any other networked device, each possesses a distinct MAC address that sets it apart from the rest.
The Structure of a MAC Address: Breaking Down the Components A MAC address is a series of six pairs of hexadecimal digits, separated by colons or hyphens. These pairs are divided into two parts: the Organizationally Unique Identifier (OUI) and the NIC identifier. The OUI identifies the manufacturer of the NIC, while the NIC identifier is unique to the device itself.
MAC Addresses and Local Network Communication In a local area network (LAN), MAC addresses play a critical role in facilitating communication. When a device sends data, it attaches the recipient’s MAC address to the data packet. Network devices, such as switches, use MAC addresses to determine the correct path for data to reach its destination. This efficient process ensures that data is directed only to the intended recipient.
Role of MAC Addresses in Data Transmission
1. Addressing Data Packets: When a device within a local network wants to send data to another device, it doesn’t just throw the data into the network abyss. Instead, it attaches the recipient’s MAC address to the data packet. This acts like a virtual postal address, telling the network where the data is intended to go.
2. Efficient Data Forwarding: Network devices, especially switches, rely on MAC addresses to make informed decisions about data forwarding. Switches maintain a dynamic table known as the MAC address table, which maps MAC addresses to specific ports. When a switch receives a data packet, it checks the table to find the MAC address associated with the recipient device. It then forwards the packet only to the port associated with that MAC address, minimizing unnecessary traffic.
3. Reducing Network Congestion: Imagine a bustling office with numerous devices sending data simultaneously. Without MAC addresses, data packets might flood the network, causing congestion and delays. Thanks to MAC addresses, data packets are directed only to the device that matches the destination MAC address. This targeted approach reduces network congestion and enhances overall efficiency.
Unicast, Broadcast, and Multicast MAC Addresses
1. Unicast MAC Addresses: Precision Point-to-Point Communication Unicast communication is akin to a private conversation between two individuals in a crowded room. Unicast MAC addresses are used for one-to-one communication, where a sender directs data packets to a specific recipient. When a device wants to send data to another device, it includes the recipient’s MAC address in the packet. Network switches use this address to ensure that the data reaches only the intended device, enhancing data privacy and efficiency.
2. Broadcast MAC Addresses: Addressing the Entire Ensemble Broadcast communication is like making an announcement to an entire room, ensuring that everyone receives the message. Broadcast MAC addresses are utilized for one-to-all communication within a network. When a device sends data with a broadcast MAC address, switches forward the data to all devices within the local network. This type of communication is useful for scenarios where information needs to be disseminated to all devices, such as network discovery or updates.
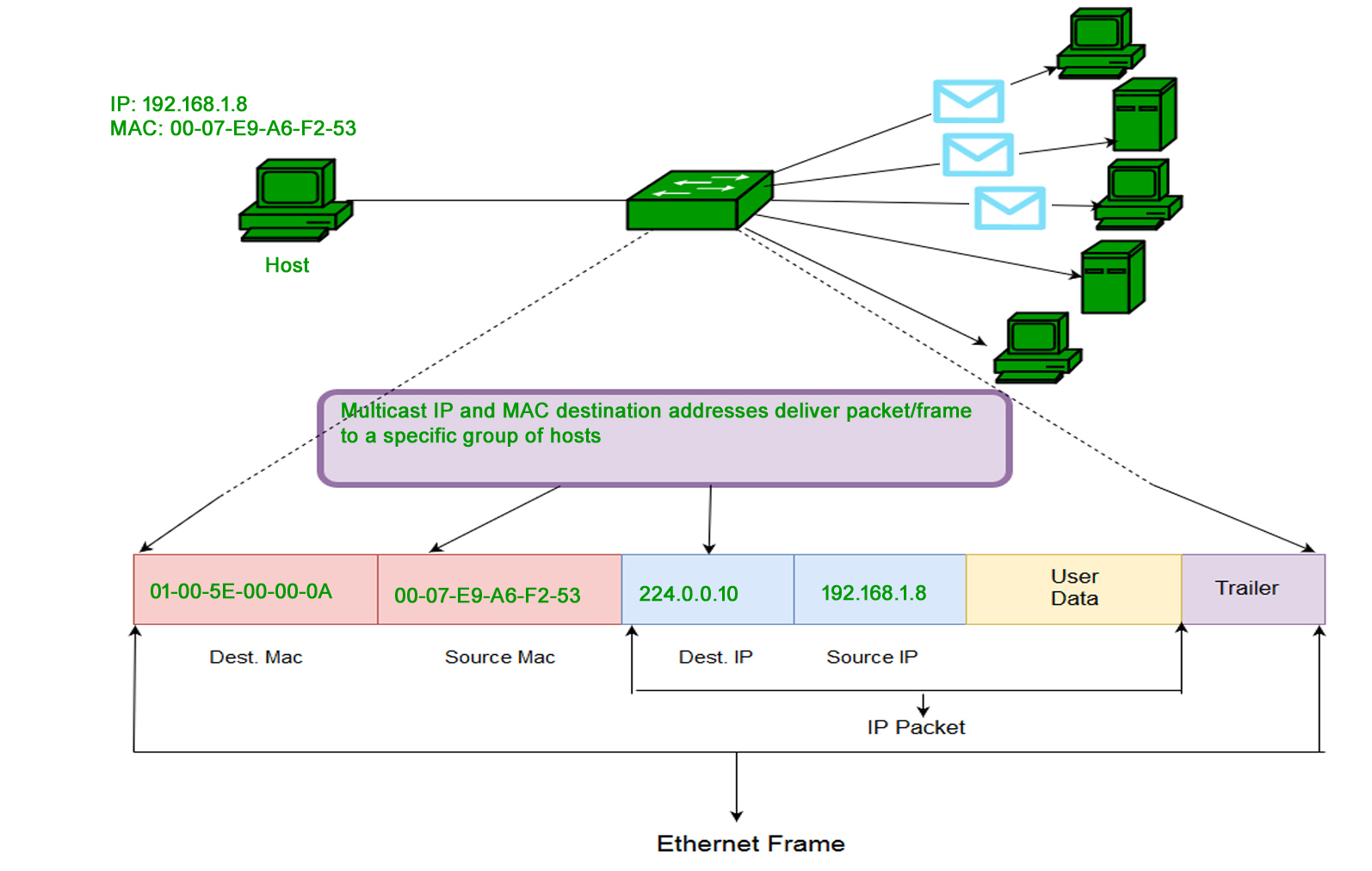
3. Multicast MAC Addresses: Directed Group Communication Multicast communication is akin to addressing a specific group of people with a common interest. Multicast MAC addresses enable one-to-many communication, directed to a select group of devices within a network. Devices that belong to the multicast group share a common multicast MAC address. When a device sends data with a multicast address, the switches forward the data to the devices belonging to that multicast group, optimizing bandwidth usage and reducing unnecessary traffic.
MAC Address vs. IP Address
| Aspect | MAC Address | IP Address |
|---|---|---|
| Function | Hardware identifier at data link layer for LAN | Logical address for routing data across networks |
| Format | Six pairs of hexadecimal digits | Four numerical values separated by dots |
| Scope | Locally significant within a single LAN | Globally significant across networks |
| Uniqueness | Unique for each device on the same LAN | May not always be unique due to dynamic IP assignment |
| Security | Basic access control within LAN | Used in various security measures and controls |
| Communication Role in LAN | Used for local communication between devices | Not used for direct communication within LAN |
| Communication Role in Networks | Not used for routing data between networks | Used for routing data across different networks |
MAC Address Spoofing and Security
| Aspect | MAC Address Spoofing |
|---|---|
| Definition | Changing or impersonating MAC address to masquerade as another device |
| Purpose | Unauthorized access, bypassing security controls, launching attacks |
| Implications | Unauthorized network access, evading security measures, DoS attacks |
| Preventive Measures | MAC filtering, port security, network monitoring, encryption, authentication protocols |
| Detection and Mitigation | Behavior analysis, intrusion detection systems |
Changing MAC Addresses and Privacy Concerns
1. The Art of Changing MAC Addresses:
- Definition: Changing a device’s MAC address involves modifying the unique identifier associated with its network interface.
- Purpose: Some users change MAC addresses for legitimate reasons, such as troubleshooting network issues, avoiding network restrictions, or protecting their privacy.
2. Privacy Implications and Anonymity:
- MAC Address Tracking: MAC addresses are unique identifiers that can potentially be used to track user movements within physical spaces, raising privacy concerns.
- MAC Randomization: To address these concerns, modern devices may employ MAC randomization, generating temporary MAC addresses to prevent long-term tracking.
3. Challenges for Network Management:
- MAC Address Spoofing: While legitimate users might change MAC addresses for privacy reasons, malicious users might do so to evade network security controls and engage in unauthorized activities.
- Network Troubleshooting: Changing MAC addresses can complicate network management and troubleshooting efforts, making it difficult to identify and track specific devices.
4. Security vs. Privacy: Striking the Balance:
- Security Concerns: Constantly changing MAC addresses can raise suspicions, as it’s a tactic used by some malicious actors. Network administrators might regard such behavior as potentially harmful.
- Privacy Protection: On the other hand, the ability to change MAC addresses can be crucial for safeguarding users’ privacy, particularly when connecting to public Wi-Fi networks.
MAC Filtering and Network Access Control
| Aspect | MAC Filtering | Network Access Control (NAC) |
|---|---|---|
| Definition | Control network access based on MAC addresses | Techniques and policies to manage network access |
| Implementation | Create whitelist/blacklist of MAC addresses | Authentication, authorization, compliance assessment |
| Benefits | Prevent unauthorized access, enhance security | Threat mitigation, policy enforcement, guest management |
| Authorized Device Management | Ensures only approved MACs access the network | Identifies and isolates compromised devices |
| Network Segmentation | Segments network into zones with varying access | Enforces security policies |
| Types | Allow List (Whitelist), Deny List (Blacklist), Dynamic Filtering | Controls access for users and devices |
MAC Addresses in Wireless Networks
| Aspect | Wi-Fi and MAC Addresses |
|---|---|
| Wireless Communication | Devices communicate using radio waves in wireless networks |
| Access Points (APs) | APs bridge wired and wireless networks, manage communication |
| Role in Wi-Fi Authentication | MAC addresses used to identify and authenticate devices |
| Association Process | Devices associate with APs, using MAC addresses |
| Authentication Exchange | Device’s MAC address sent to AP for authentication |
| Efficient Data Flow | Data divided into frames, each with MAC addresses |
| Data Framing | Frames contain sender’s and recipient’s MAC addresses |
Conclusion
In the ever-evolving landscape of digital connectivity, where information traverses the airwaves and data packets crisscross networks, the unassuming yet powerful Media Access Control (MAC) addresses stand as the networking signatures that silently guide the symphony of communication. As we conclude our exploration into the world of MAC addresses in wireless networks, we are reminded of their pivotal role in shaping the seamless flow of data, ensuring security, and enabling the interconnected world we inhabit.
FAQs
A MAC address, or Media Access Control address, is a unique identifier assigned to the network interface of a wireless device. It plays a crucial role in wireless network communication, facilitating data transmission, authentication, and device identification.
During the process of connecting to a Wi-Fi network, a device’s MAC address is sent to the access point. The access point uses this MAC address for authentication, ensuring that only authorized devices can join the network.
Yes, MAC addresses can be changed or spoofed, which involves altering the device’s MAC address to mimic another valid address. This can be used to gain unauthorized access or mask the identity of a device. However, security measures like MAC address filtering can help mitigate this risk.
MAC addresses are included in data frames transmitted within wireless networks. These addresses guide the data frames to their intended recipients, helping to ensure efficient and accurate data transmission.
Read Also
Related posts:
- AMC Full Form: Benefits, Components, Needs, Advantage
- ORS Full Form: Dehydration, Myths, Flavors, Varieties & Facts
- PCC Full Form: Importance, Types, Application Process
- PAN Full Form: Legal Provisions, Regulations,
- BRB Full Form: Productive, Routine, Distractions
- MCD Full From: Introduction, Responsibility, Challenges
- CT Scan Full Form: Scans, price, Advantages
- USA Full Form: History, Economics,Technology, culture




















