In the ever-evolving landscape of virtual interactions, the want for seamless and secure get entry to to numerous structures has emerge as paramount. Enter Single Sign-On SSO ID login – a transformative authentication approach designed to simplify the consumer revel in and beautify protection throughout the digital spectrum.
- What is SSO ID Login?
- Process of SSO ID Rajasthan Registration
- Process of SSO ID Login
- How to update SSO ID Jan Aadhaar ID Number
- Enhancing Security Measures with SSO ID Login
- Integrating SSO ID Login into Your Business Ecosystem
- Navigating the SSO ID Login Landscape
- Boosting Productivity Through SSO ID Login
- Frequently Asked Questions (FAQs)
Introduction
- In a world wherein people juggle severa online bills, every covered by means of its very own set of credentials, SSO ID Login emerges as a beacon of convenience. It lets in customers to log in just as soon as, granting them get entry to to a large number of applications and offerings with out the trouble of time and again coming into usernames and passwords. This now not handiest streamlines the user experience but additionally addresses security worries by means of decreasing the capability points of vulnerability.
- At its middle, SSO ID Login is a centralized authentication device that empowers customers with a unified digital identity. This identification is authenticated via a single set of login credentials, frequently managed through a imperative server. Once authenticated, customers acquire a token that serves as a virtual key, unlocking doors to various systems seamlessly.
- This blog adventure will discover the nuances of SSO ID login, unraveling its functionalities, advantages, and the impact it has on consumer comfort and security. We’ll delve into the mixing procedure, highlight actual-international fulfillment tales, and offer insights into the future of get entry to control within the virtual era.
What is SSO ID Login?
Here’s a breakdown of key factors within SSO ID Login:
- Single Sign-On (SSO): SSO enables users to authenticate as soon as and gain get admission to to multiple packages without the need to re-enter credentials for each provider. This streamlines the login process and complements user comfort.
- Identification (ID) Login: The “ID Login” thing emphasizes the use of a unique identifier, which include a username or electronic mail deal with, along side a corresponding password or different authentication factors. This aggregate paperwork the consumer’s credentials for getting access to the SSO-enabled system.
- Centralized Authentication: SSO ID Login often involves a centralized authentication server or identification provider. This server verifies the user’s identity and problems a token or proof of authentication, allowing get entry to to diverse linked packages.
- Token-Based Access: After a success authentication, users get hold of a token that serves as a digital key. This token is supplied to different applications or offerings inside the SSO environment to validate the consumer’s identity with out the need for reauthentication.
- Cross-Platform Access: SSO ID Login helps get admission to across extraordinary structures and domains. Users can seamlessly navigate between various applications and offerings with out the hassle of coping with multiple units of credentials.
- Security Protocols: SSO implementations regularly contain robust security protocols to guard consumer identities and sensitive statistics. Common standards consisting of OAuth (Open Authorization) and SAML (Security Assertion Markup Language) are regularly used to make sure steady authentication.
- User Experience: The primary purpose of SSO ID Login is to decorate the user enjoy by using simplifying the login system. Users gain from reduced friction, faster get right of entry to to assets digital interaction.
- Integration with Identity Providers: SSO ID Login structures can be integrated with identity vendors (e.G., Microsoft Azure AD, Google Identity Platform) to leverage present person databases and authentication mechanisms, streamlining the onboarding system.
Process of SSO ID Rajasthan Registration
To register for SSO ID in Rajasthan, you commonly need to comply with these steps:
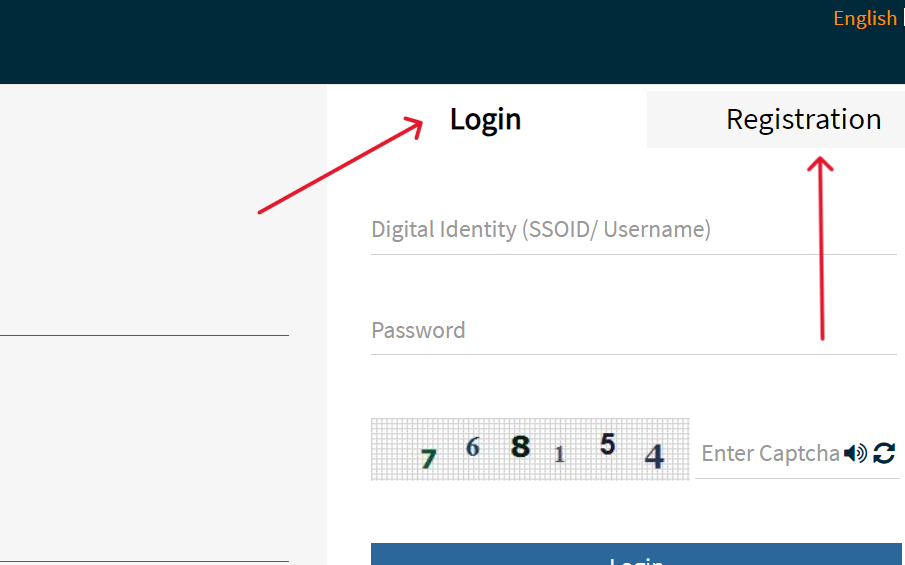
1. Visit the Rajasthan Single Sign-On (SSO) Portal:
- Go to the respectable Rajasthan SSO portal. The net address can also range, so it is really helpful to search for the present day and legitimate SSO ID Login portal for Rajasthan.
2. Click on “Register” or “Create Account”:
- Look for the “Register” or “Create Account” choice at the portal’s homepage and click on it to provoke the registration procedure.
3. Provide Personal Details:
- Fill within the required data, which may encompass your name, date of beginning, email cope with, cell number, and other applicable info. Make certain to go into accurate data because it will be used to create your SSO ID.
4. Choose a Username and Password:
- Select a completely unique username and a strong password on your SSO ID Login. The password may additionally want to fulfill sure criteria, such as a minimum length and inclusion of special characters.
5. Verify Your Mobile Number and Email:
- You can be required to affirm your mobile quantity and electronic mail address thru a one-time password (OTP) sent for your registered mobile number and e-mail.
6. Complete the Registration Process:
- Follow the on-display commands to finish the registration technique. This may additionally encompass agreeing to phrases and conditions or providing extra info.
7. Log In to Your SSO Account:
- Once registered, log in to your SSO account the usage of the created username and password. You will now have access to the SSO portal and diverse e-offerings furnished by the Rajasthan government.
8. Link Aadhaar or Other Documents (if required):
- Some offerings or schemes can also require you to link your Aadhaar or other files for verification purposes. Follow the unique commands furnished on the portal for such requirements.
9. Explore Available Services:
- After a success registration, discover the listing of offerings to be had at the SSO ID Login portal. You can access numerous authorities offerings, along with making use of for certificate, checking land statistics, or availing different on line facilities.
10. Keep Your SSO ID Secure:
- Remember to keep your SSO ID Login credentials stable. Do not percentage your username and password with others to prevent unauthorized access in your account.
Process of SSO ID Login
- The Single Sign-On (SSO) ID login system can vary depending at the particular SSO device or platform you’re the usage of. Below is a popular manual that outlines the typical steps involved inside the SSO ID login process:
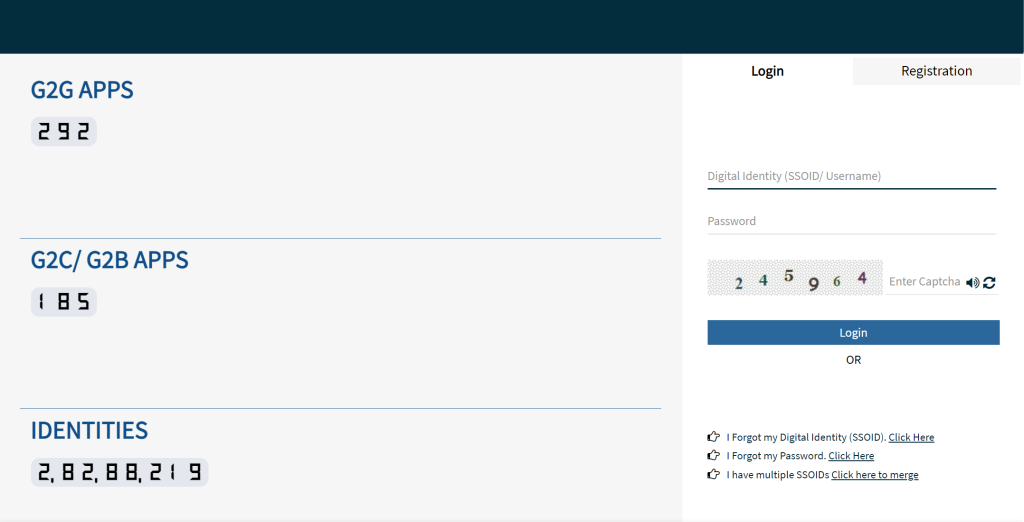
Visit the SSO Portal:
- Start through navigating to the reputable Single Sign-On portal of the organization or provider you are trying to access. The net cope with may also vary, so make certain you are using the appropriate URL.
Locate the Login Section:
- On the SSO portal homepage, discover the login phase. This is usually prominently displayed and might consist of fields for getting into your username and password.
Enter Your SSO ID Credentials:
- Input your SSO ID Login credentials, which typically consist of a username and password. Some SSO systems may additionally use additional authentication elements, including one-time passwords (OTP) despatched for your registered e-mail or cell device.
Submit Your Credentials:
- Once you have entered your username and password, click on on the “Login” or “Submit” button to ship your credentials for verification.
Authentication:
- The SSO ID Login gadget will authenticate your credentials in opposition to its centralized authentication server. If the furnished records is correct, you may be granted get right of entry to.
- The Single Sign-On (SSO) ID login system can vary depending at the particular SSO device or platform you’re the usage of. Below is a popular manual that outlines the typical steps involved inside the SSO ID login process:
Visit the SSO Portal:
- Start through navigating to the reputable Single Sign-On portal of the organization or provider you are trying to access. The net cope with may also vary, so make certain you are using the appropriate URL.
Locate the Login Section:
- On the SSO portal homepage, discover the login phase. This is usually prominently displayed and might consist of fields for getting into your username and password.
Enter Your SSO ID Credentials:
- Input your SSO ID credentials, which typically consist of a username and password. Some SSO systems may additionally use additional authentication elements, including one-time passwords (OTP) despatched for your registered e-mail or cell device.
Submit Your Credentials:
- Once you have entered your username and password, click on on the “Login” or “Submit” button to ship your credentials for verification.
Authentication:
- The SSO gadget will authenticate your credentials in opposition to its centralized authentication server. If the furnished records is correct, you may be granted get right of entry to.
How to update SSO ID Jan Aadhaar ID Number
Visit the SSO Portal:
- Start by using journeying the official Single Sign-On (SSO) portal in which you to begin with registered or in which you control your account.
Log In to Your SSO Account:
- Log in in your SSO ID Login account the use of your present credentials, along with your username and password.
Navigate to Profile or Account Settings:
- Look for a segment associated with your profile or account settings. This is generally wherein you can control and update your private records.
Locate Aadhaar ID Section:
- Within your profile or account settings, discover the phase specifically associated with Aadhaar ID or personal information.
Update Aadhaar Information:
- Follow the on-display commands to replace or input your Aadhaar ID wide variety. You may be required to offer additional records for verification functions.
Verify Changes (if required):
- Some SSO ID Login platforms may additionally require extra verification steps to make sure the accuracy of the up to date Aadhaar data. This should contain OTP verification or other authentication strategies.
Save or Submit Changes:
- After updating your Aadhaar ID, ensure to save or publish the modifications. Look for a “Save” or “Submit” button within the profile or account settings.
Check Confirmation:
- Once the changes are stored, test for any confirmation message or notification indicating that your Aadhaar ID records has been successfully updated.
It’s important to be aware that the stairs noted above are standard hints, and the real process may additionally range depending on the particular SSO platform or provider provider. Additionally, if the SSO ID Login is linked to a government initiative, consisting of Jan Aadhaar, there may be unique methods outlined through the concerned authorities branch.
Enhancing Security Measures with SSO ID Login
1. Centralized Authentication:
- SSO operates on a centralized authentication model. A singular, secure authentication server verifies user identities, lowering the attack surface compared to dealing with credentials across more than one structures. This centralized approach helps higher control over get admission to factors and enhances safety monitoring.
2. Reduced Password Fatigue:
- Users frequently inn to weak passwords or reuse them across more than one systems due to the sheer number of accounts they manage. SSO alleviates this with the aid of requiring users to recollect most effective one set of credentials, making it greater viable to put in force and implement robust password policies, along with length and complexity requirements.
3. Multi-Factor Authentication (MFA):
- Many SSO ID Login systems assist Multi-Factor Authentication (MFA) as an extra layer of safety. By requiring users to provide more than one types of identity (including passwords, biometrics, or one-time codes), SSO strengthens the authentication technique, making it drastically more difficult for unauthorized customers to gain get entry to.
4. Token-Based Access:
- SSO makes use of tokens to validate a person’s identification across connected programs. These tokens are time-touchy and provide a secure manner of getting access to services without exposing touchy credentials. Even if intercepted, tokens have a confined lifespan, mitigating the risk of unauthorized get admission to.
5. Granular Access Control:
- Administrators can put into effect granular get admission to manage policies through SSO ID Login. This ensures that users only have get admission to to the assets and services necessary for his or her roles, minimizing the effect of a compromised account and preventing lateral motion within the occasion of a safety breach.
6. Audit Trails and Monitoring:
- SSO systems regularly come prepared with strong logging and tracking abilities. Detailed audit trails tune user activities, allowing administrators to become aware of and respond to suspicious behavior right away. This proactive approach enhances the general protection posture by enabling swift action in opposition to capability threats.
7. Integration with Security Standards:
- SSO implementations adhere to set up safety standards such as OAuth and Security Assertion Markup Language (SAML). Compliance with those requirements ensures stable records alternate between parties concerned within the authentication procedure, minimizing vulnerabilities and promoting interoperability.
8. Continuous Security Updates:
- SSO companies regularly replace their systems to patch vulnerabilities and address emerging security threats. Users and administrators advantage from those updates, making sure that the SSO infrastructure stays resilient in opposition to evolving cyber threats.
9. User Education and Awareness:
- SSO ID Login contributes to a greater secure surroundings by using fostering consumer schooling and consciousness. Users, armed with a better understanding of safety high-quality practices, are much less in all likelihood to fall sufferer to phishing attempts or have interaction in volatile on line conduct.
10. Regular Security Audits:
- Organizations imposing SSO often conduct everyday security audits to evaluate the system’s resilience. These audits help identify and remediate ability vulnerabilities, ensuring that the SSO infrastructure remains a sturdy layer of protection towards cyber threats.
In conclusion, SSO ID login, when implemented thoughtfully, stands as a cornerstone in fortifying digital get admission to. By embracing centralized authentication, multi-aspect security measures, and a proactive security stance, organizations can leverage the total capability of SSO to enhance the security posture of their digital ecosystems.
Integrating SSO ID Login into Your Business Ecosystem
1. Define Objectives and Scope:
- Begin via certainly defining the targets of integrating SSO into your enterprise ecosystem. Identify the structures, packages, and offerings with a view to be a part of the SSO implementation. Determine whether the point of interest is on internal structures, client-going through portals, or both.
2. Select an SSO Solution:
- Choose an SSO solution that aligns with your business requirements. Consider factors along with scalability, compatibility with present systems, security features, and ease of integration. Popular SSO protocols consist of OAuth and Security Assertion Markup Language (SAML).
3. Assess Existing Infrastructure:
- Evaluate your contemporary IT infrastructure to ensure compatibility with the chosen SSO solution. Identify capability integration demanding situations and plan for any essential updates or modifications to current systems.
4. User Identity Management:
- Establish a strong user identification control system. Integrate the SSO solution along with your identification issuer, which includes Active Directory or LDAP (Lightweight Directory Access Protocol), to make certain correct and steady person authentication.
5. User Provisioning and Deprovisioning:
- Implement automated approaches for person provisioning and deprovisioning. When personnel join or leave the enterprise, their get right of entry to rights need to be seamlessly up to date across all included platforms via SSO.
6. Customize the User Experience:
- Tailor the SSO login experience to align along with your emblem and person expectancies. Consider customizing the login web page and incorporating your business logo for a consistent and expert look.
7. Implement Multi-Factor Authentication (MFA):
- Enhance safety with the aid of incorporating Multi-Factor Authentication (MFA) into the SSO login technique. MFA adds an additional layer of verification, commonly concerning a 2nd shape of identity consisting of a one-time code or biometric authentication.
8. Educate Users:
- Provide comprehensive schooling and communication to customers about the brand new SSO login technique. Address any worries, make clear the blessings, and manual users on the way to navigate the updated authentication workflow.
9. Test Rigorously:
- Conduct thorough testing before deploying the SSO integration into the live surroundings. Test special eventualities, person roles, and potential area instances to make certain a clean and error-loose consumer revel in.
10. Monitor and Optimize:
- Implement tracking tools to tune SSO performance and user sports. Regularly assessment logs and analytics to perceive any anomalies or potential protection troubles. Continuously optimize the SSO integration based totally on person feedback and evolving business necessities.
11. Compliance and Data Privacy:
- Ensure that your SSO implementation complies with relevant statistics protection and privacy policies. Safeguard person data and adhere to enterprise-precise compliance requirements.
Navigating the SSO ID Login Landscape
This guide navigates via the important capabilities and considerations, imparting a comprehensive knowledge of the SSO ID login environment.
1. Centralized Authentication:
- SSO prospers on centralized authentication, in which a unmarried, steady server verifies user identities. This centralization streamlines get right of entry to management and enhances safety by minimizing the attack floor.
2. User Convenience Across Platforms:
- SSO lets in users to get right of entry to a couple of packages with a unmarried set of credentials. Whether navigating inner systems, cloud services, or third-celebration packages, customers revel in the ease of streamlined access.
3. Interoperability with Standards:
- Successful SSO implementations frequently adhere to broadly identified requirements which include OAuth and Security Assertion Markup Language (SAML). This guarantees compatibility and interoperability with numerous structures and packages.
4. Integration with Identity Providers:
- SSO systems can integrate seamlessly with identification companies (IdPs), including Microsoft Azure AD or Google Identity Platform. This integration streamlines consumer identity management and leverages current authentication mechanisms.
5. Token-Based Authorization:
- SSO is predicated on token-primarily based authorization. After a user authenticates, they acquire a token that serves as a virtual key, granting get entry to to linked applications with out the need for non-stop reauthentication.
6. Multi-Factor Authentication (MFA):
- Security is strengthened through the implementation of Multi-Factor Authentication (MFA). This additional layer of verification, which includes one-time codes or biometrics, provides resilience towards unauthorized get entry to.
7. Granular Access Control:
- Administrators can implement granular get entry to manipulate policies, defining the level of get right of entry to customers should one-of-a-kind sources. This ensures that users best access the statistics and functionalities necessary for their roles.
8. Logging and Auditing:
- Robust logging and auditing abilties provide administrators with insights into user activities. Detailed logs useful resource in monitoring user actions and identifying any suspicious behavior or protection incidents.
9. User Provisioning and Deprovisioning:
- SSO streamlines consumer provisioning and deprovisioning. When a user joins or leaves the employer, get right of entry to rights are efficiently controlled throughout all connected systems.
10. Cross-Domain Access:
- SSO helps access throughout one-of-a-kind domains and platforms. Users can seamlessly navigate between inner systems, cloud applications, and external services with out the want for separate logins.
11. Customization and Branding:
- SSO answers often allow for customization of the login experience. Businesses can brand the login web page, developing a cohesive and expert consumer interface aligned with their corporate identification.
12. Password Policies and Security Standards:
- SSO allows businesses to put in force constant and strong password rules. Adherence to security standards guarantees that consumer credentials are covered and meet industry fine practices.
Boosting Productivity Through SSO ID Login
1. Eliminating Password Fatigue:
- SSO liberates customers from the burden of dealing with more than one units of usernames and passwords. With a single set of credentials, the want to keep in mind and input complex passwords for various programs is eliminated, assuaging password fatigue and saving precious time.
2. Seamless Access Across Applications:
- SSO provides customers with seamless get admission to throughout a spectrum of applications and systems. Whether it’s electronic mail, undertaking control equipment, or collaboration software program, customers can navigate effortlessly with out the interruption of repeated logins.
3. Reduced Downtime and Friction:
- With SSO, the login manner becomes a one-time affair. This discount in login events interprets to less downtime and friction in each day tasks, allowing users to awareness on their responsibilities in place of navigating authentication hurdles.
4. Efficient Onboarding and Offboarding:
- SSO streamlines consumer onboarding and offboarding techniques. New personnel advantage quick get admission to to necessary tools, and departing personnel have their get entry to right away revoked. This performance is mainly impactful for HR departments and IT teams managing consumer money owed.
5. Enhanced Collaboration:
- Collaborative efforts are expedited with SSO. Team members can seamlessly get admission to shared assets and collaborate in real-time with out the interruption of repeated logins. This fosters a collaborative work environment, boosting universal productivity.
6. Faster Task Execution:
- SSO speeds up mission execution by way of putting off the need to time and again log in to numerous programs during the day. Users can rapidly transition among equipment, lowering the time spent on mundane authentication approaches.
7. Mobile Productivity:
- With SSO, users can maintain productivity on the move. Mobile applications and gadgets are seamlessly included into the SSO environment, allowing users to get right of entry to vital gear and sources from everywhere with a single login.
8. Centralized Access Control:
- Administrators advantage from centralized access manipulate. Managing consumer access rights turns into greater efficient, ensuring that personnel have get admission to simplest to the resources and applications relevant to their roles.
9. Consistent User Experience:
- SSO contributes to a regular consumer experience. The uniformity of the login process and interface across various programs reduces user confusion and contributes to a more user-friendly digital environment.
10. Security and Compliance:
- SSO enhances safety via implementing robust password guidelines and facilitating short deprovisioning of get right of entry to. This not most effective safeguards touchy facts but additionally guarantees compliance with security standards and policies.
11. Quick Recovery from System Failures:
- In the event of gadget disasters or crashes, SSO aids in brief recovery. Users can hastily regain get admission to to their programs as soon as the gadget is restored, minimizing disruptions and maximizing uptime.
12. User Empowerment:
- SSO empowers users through presenting them with a tool that enhances their efficiency. This empowerment contributes to a positive paintings tradition, in which employees feel supported by technology in preference to hindered by way of it.
13. Integration with Cloud Services:
- SSO seamlessly integrates with cloud services, allowing corporations to leverage the advantages of cloud computing. This integration contributes to a greater agile and flexible IT infrastructure, assisting modern commercial enterprise needs.
Frequently Asked Questions (FAQs)
Single Sign-On (SSO) ID login is an authentication system that enables customers to get admission to more than one programs or offerings with a unmarried set of login credentials. It simplifies the login enjoy by way of removing the want to go into exclusive usernames and passwords for each software.
SSO complements security via centralizing authentication, reducing the wide variety of credentials customers want to manipulate. It frequently carries multi-aspect authentication (MFA) and permits for greater sturdy access control, minimizing the chance of unauthorized access.
Yes, SSO may be implemented for both inner programs inside an organization and external applications or services accessed by personnel, partners, or customers.
Related posts:
- Jaa Lifestyle Login: Portal, Benefits, Product and Services
- Spice Money Login: Guide, Seamless Experience, App Login
- Hotstar Login: Creating Account, Troubleshooting, Premium vs Free
- Staff Login: Right Authentication, Challenges, SSO, Training
- AWPL Login: Features, Authentication Methods, Troubleshooting
- IFHRMS Login: Organizations, Security, Troubleshooting




















