This comprehensive guide aims to get to the bottom of the intricacies of UDIN login, offering specialists with a roadmap to seamlessly comprise this authentication device into their workflow. From the fundamental standards of UDIN to realistic step-with the aid of-step courses on registration and login, we embark on a journey to demystify UDIN and exhibit its pivotal role in setting up accept as true with, compliance, and efficiency within the professional sphere.
- Navigating the UDIN Login Portal – Step-by-Step Login Guide
- The Why and How of UDIN Login Registration
- Ensuring Document Integrity – UDIN Login and Its Verification
- UDIN Login and Compliance – Navigating Requirements
- Troubleshooting UDIN Login Issues – Guide
- UDIN Login and Client Trust – Building a Reputation
- Mobile Access to UDIN Login – Anytime, Anywhere Authentication
- UDIN Login and Digital Signatures
- Frequently Asked Questions (FAQs)
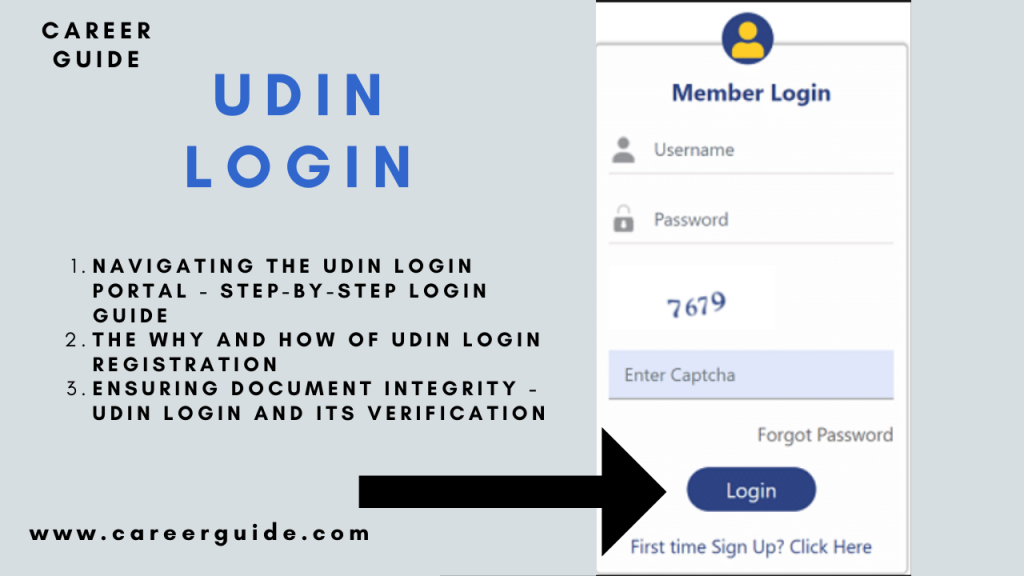
Navigating the UDIN Login Portal - Step-by-Step Login Guide
The first step on this journey includes navigating the UDIN login portal successfully. In this phase, we gift a comprehensive, step-by using-step guide to help you in seamlessly having access to the UDIN gadget.
1-Step: Accessing the UDIN Portal
Begin your UDIN login adventure through having access to the authentic UDIN portal. This is typically achieved through an internet browser. Ensure that you are the usage of a secure and updated browser for a easy experience.
2-Step: Choosing the ‘Login’ Option
Once at the UDIN portal’s homepage, discover and click on at the ‘Login’ option. This is your gateway to the authentication system. Make sure you have got your login credentials equipped, which includes your UDIN consumer ID and password.
3-Step: Entering User ID and Password
Upon choosing ‘Login,’ you may be directed to a page prompting you to enter your UDIN consumer ID and password. Carefully enter the credentials associated with your UDIN registration. Double-test for accuracy to keep away from login issues.
4-Step: Two-Factor Authentication (if applicable)
Many steady portals, along with UDIN, implement -aspect authentication for an brought layer of safety. This may additionally involve receiving a code for your registered mobile variety or electronic mail. Enter the code right away to continue.
5-Step: Dashboard Access
Upon a hit authentication, you will benefit access in your UDIN dashboard. This is your significant hub for handling and authenticating documents. Take a second to familiarize yourself with the dashboard layout and to be had options.
6-Step: Document Authentication
Navigate to the applicable section in the dashboard to provoke the document authentication method. This can also contain uploading the record and acquiring the UDIN for verification purposes. Follow the on-screen commands to finish this crucial step.
7-Step: Logout Securely
Once you have finished your obligations, make certain you sign off securely. This step is vital for maintaining the confidentiality of your account and stopping unauthorized get entry to. Look for the ‘Logout‘ or ‘Sign Out’ alternative within the portal.
8-Step: Troubleshooting Tips (Optional)
If you come upon any issues for the duration of the login method, talk over with the troubleshooting phase in our manual for realistic answers. Common troubles along with forgotten passwords or two-thing authentication hiccups can regularly be resolved swiftly.
The Why and How of UDIN Login Registration
Before delving into the intricacies of UDIN login, it is crucial to recognize the significance of UDIN registration. In this phase, we discover the motives in the back of the registration technique and offer an in depth step-with the aid of-step guide on a way to sign in, ensuring that professionals are geared up with the essential credentials to leverage the energy of UDIN.
Why UDIN Registration Matters:
Document Authentication Assurance:
UDIN serves as a completely unique identifier for expert documents, adding a further layer of warranty regarding their authenticity. Registration is the gateway to acquiring and utilising those specific identity numbers.
Regulatory Compliance:
Many expert our bodies and regulatory authorities mandate the use of UDIN for document authentication. Registration ensures compliance with those requirements, safeguarding specialists against legal and regulatory troubles.
Enhanced Professional Credibility:
By registering for UDIN, specialists signal their dedication to upholding the best standards of file authenticity. This commitment, in turn, enhances their credibility within the eyes of clients, stakeholders, and regulatory our bodies.
Client Trust and Transparency:
Clients value transparency in expert transactions. Registering for UDIN and using it in file authentication instills trust with the aid of presenting clients with a verifiable way of confirming the legitimacy of the documents they acquire.
How to Register for UDIN:
Visit the Official UDIN Portal:
Begin the registration system by way of accessing the official UDIN portal via a secure web browser. Ensure which you are at the legitimate website to avoid potential safety dangers.
Navigate to the Registration Section:
Look for the ‘Registration’ or ‘Sign Up’ phase on the portal’s homepage. Click on this selection to provoke the registration process.
Provide Personal and Professional Information:
Fill inside the required fields with correct non-public and professional data. This may additionally encompass your call, touch information, professional qualifications, and every other statistics deemed vital for registration.
Create a Secure Password:
Choose a sturdy and stable password to your UDIN account. Ensure that it meets the required criteria for complexity to enhance the security of your account.
Verification Process:
Some registration strategies may also involve a verification step. This may want to encompass e mail verification or cellular quantity verification. Follow the on-screen instructions to finish this step.
Accept Terms and Conditions:
Review the terms and conditions related to UDIN registration. Accept these phrases to continue with the registration method.
Confirmation and User ID Generation:
Upon a hit registration, you will receive a confirmation message, and your UDIN person ID could be generated. This user ID, in conjunction with your password, might be essential for destiny logins.
Ensuring Document Integrity - UDIN Login and Its Verification
The Unique Document Identification Number (UDIN) performs a pivotal function in this method with the aid of imparting a unique identifier for every authenticated document. In this segment, we discover how the UDIN login and verification manner contribute to maintaining record integrity.
Understanding the Significance of UDIN in Document Authentication:
Unique Identifier:
UDIN serves as a special fingerprint for each professional file. When a document is issued or authenticated, it’s far assigned a completely unique UDIN, making it without difficulty traceable and verifiable.
Protection Against Tampering:
The inherent forte of UDIN acts as a deterrent towards file tampering. Any try to modify or manage a report will become obtrusive while the UDIN is verified, preserving the record’s originality.
Verification by way of Stakeholders:
Various stakeholders, which includes customers, regulatory our bodies, and other specialists, can independently affirm the authenticity of a record by pass-referencing its UDIN. This verification manner fosters transparency and believe.
The UDIN Login and Verification Process:
Accessing the UDIN Portal:
Begin the process by means of logging into the UDIN portal using your registered user ID and password. Ensure a steady connection for the safety of touchy statistics.
Selecting the Document for Verification:
Navigate to the verification section inside the portal. Choose the file you desire to affirm by means of coming into its applicable information, inclusive of the UDIN assigned to it throughout the authentication technique.
Initiating the Verification Request:
Follow the on-display screen activates to initiate the verification request. This can also involve uploading a copy of the report or entering precise records associated with the file.
Cross-Referencing with UDIN Database:
The portal’s machine pass-references the entered UDIN with the UDIN database to affirm the document’s authenticity. If the UDIN is legitimate, the file is confirmed as real.
Verification Outcome:
The verification procedure will yield considered one of outcomes – both the record is established correctly, confirming its authenticity, or the report fails verification, indicating a capacity trouble with its integrity.
Benefits of UDIN Verification:
Enhanced Trustworthiness:
Stakeholders can agree with that documents bearing a valid UDIN have gone through a stringent authentication system, instilling self belief within the reliability of the records provided.
Compliance Assurance:
Verification via UDIN aligns with regulatory compliance requirements, making sure that specialists adhere to enterprise requirements and felony duties.
Swift Resolution of Disputes:
In case of disputes or discrepancies, UDIN verification presents an green manner of resolving troubles by way of presenting a clear and traceable history of the record’s authentication.
UDIN Login and Compliance - Navigating Requirements
In this section, we discover the intersection of UDIN login and compliance, providing insights into how experts can navigate regulatory necessities seamlessly.
Understanding the Role of UDIN in Compliance:
Mandatory Usage in Some Sectors:
In positive expert sectors, regulatory bodies mandate the use of UDIN for report authentication. This requirement goals to standardize and beautify the authenticity of files within those industries.
Proof of Authentication:
UDIN acts as concrete proof that a report has gone through an intensive authentication system. This proof is crucial in assembly compliance standards and demonstrating a dedication to obvious and truthful professional practices.
Regulatory Recognition:
Many regulatory government recognize the significance of UDIN in ensuring record integrity. Professionals who use UDIN for authentication align with those standards, fostering a harmonious relationship with regulatory our bodies.
Navigating UDIN Login for Compliance:
Stay Informed About Regulatory Requirements:
Regularly update yourself on the regulatory requirements unique in your professional quarter. Understand whether or not UDIN authentication is remitted and if so, get yourself up to speed with the associated hints.
Incorporate UDIN into Document Authentication Workflow:
Integrate the usage of UDIN into your preferred report authentication workflow. This proactive approach ensures that compliance is seamlessly woven into your every day professional practices.
Secure UDIN Login Credentials:
Recognize the sensitivity of UDIN login credentials and put in force sturdy safety features. Compliance often includes safeguarding customer information and touchy facts, making steady login practices critical.
Regularly Audit and Review Processes:
Conduct ordinary audits of your record authentication procedures to make sure ongoing compliance. This consists of verifying that UDIN is always used in which required and that the authentication workflow aligns with regulatory expectancies.
Troubleshooting UDIN Login Issues - Guide
In this section, we provide a realistic guide to troubleshoot common UDIN login troubles, ensuring that specialists can conquer demanding situations unexpectedly and get entry to the device without difficulty.
1. Forgotten Password:
Issue: Unable to log in because of a forgotten password.
Solution:
- Click at the “Forgot Password” or comparable hyperlink on the login page.
- Follow the commands to reset your password. This often entails receiving a reset hyperlink through e mail or a verification code in your registered mobile variety.
- Create a brand new strong and stable password once the reset process is entire.
2. Two-Factor Authentication Issues:
Issue: Difficulty in completing the two-element authentication process.
Solution:
- Ensure that your cell device or e mail account, used for two-component authentication, is on the market.
- Double-take a look at for typos while coming into the verification code.
- If troubles persist, touch the UDIN assist or your IT administrator for assistance.
3. Account Lockouts:
Issue: Account is locked due to more than one unsuccessful login tries.
Solution:
- Wait for the specified length stated at the login web page for account lockouts to be lifted.
- Use the password reset choice if vital, to keep away from repeated unsuccessful login tries.
4. Browser Compatibility:
Issue: Difficulties in accessing the UDIN portal the use of a specific browser.
Solution:
- Ensure you are the usage of a supported and up to date browser.
- Clear browser cache and cookies, as they may interfere with the login procedure.
- Try an exchange browser to decide if the difficulty persists.
5. Network Connectivity Problems:
Issue: Unable to log in because of community issues.
Solution:
- Check your net connection to ensure it is stable.
- If the use of a VPN, strive disabling it quickly.
- Contact your IT assist or internet service company if the issue persists.
6. Incorrect User ID:
Issue: Unable to log in due to an wrong user ID.
Solution:
- Double-check the entered user ID for accuracy, ensuring there are not any typos.
- Refer to any registration confirmation emails or documentation for the suitable consumer ID.
7. System Downtime or Maintenance:
Issue: Inability to log in because of scheduled maintenance or machine
downtime.
Solution:
- Check for any announcements regarding scheduled maintenance at the UDIN portal.
- Wait for the renovation duration to finish, and try logging in again.
UDIN Login and Client Trust - Building a Reputation
In this segment, we explore how UDIN login contributes to building a recognition of reliability and trustworthiness.
1. Transparency through Authentication:
Clients appreciate transparency of their interactions with professionals. By incorporating UDIN authentication into your file strategies, you provide customers with a tangible way of verifying the authenticity of the files they receive. This transparency instills self belief and contributes to a trusting professional dating.
2. Mitigating Document Fraud Concerns:
With the upward push of digital transactions, worries about record fraud and tampering have emerge as more commonplace. UDIN serves as a robust protection in opposition to such concerns. The use of UDIN login assures clients that the files they acquire are real, decreasing the danger of fraudulent sports and improving your credibility as a reliable expert.
3. Efficiency and Timeliness:
The streamlined authentication procedure facilitated by using UDIN login contributes to performance in report managing. Clients value experts who can supply services right away and reliably. By leveraging UDIN, you reveal a commitment to green record management, reinforcing your recognition as a dependable service company.
4. Alignment with Industry Standards:
Many expert sectors have followed UDIN as a preferred for document authentication. By using UDIN for your practice, you align yourself with industry requirements, showcasing a commitment to great practices and adherence to rules. This alignment complements your expert status and fosters patron accept as true with.
5. Enhanced Communication and Accountability:
Incorporating UDIN in your record processes allows clearer verbal exchange with clients. The unique identity variety becomes a reference factor for discussions, making sure that each parties are at the equal page regarding record authenticity. This degree of responsibility strengthens the client-expert relationship.
6. Positive Impact on Professional Reputation:
As clients become greater discerning of their choice of provider vendors, a effective professional popularity is a valuable asset. Using UDIN login no longer best demonstrates your commitment to document integrity however additionally positions you as a forward-wondering professional, contributing to an common effective reputation in your industry.
Mobile Access to UDIN Login - Anytime, Anywhere Authentication
In this segment, we explore the advantages and practicalities of cellular access to UDIN login.
1. Flexibility in Document Authentication:
Mobile get entry to to UDIN login liberates professionals from the restrictions of conventional workplace setups. Whether in transit, at customer meetings, or working remotely, the ability to authenticate documents the usage of a cell tool gives extraordinary flexibility, ensuring experts can meet closing dates and client expectancies effectively.
2. Real-Time Verification:
Mobile access facilitates actual-time document verification. Professionals can speedy reply to consumer requests or regulatory queries with the aid of gaining access to the UDIN gadget on their cell gadgets. This immediacy not most effective enhances efficiency but additionally contributes to a tradition of responsiveness and responsibility.
3. Secure Authentication on the Go:
Security is paramount, mainly when dealing with touchy professional documents. Mobile access to UDIN login is designed with strong safety features to make sure that the authentication method stays secure even if accessed from various places. Encryption protocols and secure connections shield the confidentiality of authentication activities.
4. Client Meetings and Presentations:
Professionals regularly need to authenticate documents in the course of customer conferences or shows. Mobile get right of entry to to UDIN permits seamless file verification in real-time, permitting specialists to showcase the authenticity in their work immediate. This functionality contributes to a expert photograph of preparedness and reliability.
5. User-Friendly Mobile Interface:
The cellular interface of the UDIN device is designed to be person-friendly, ensuring a clean and intuitive experience for experts gaining access to it on their smartphones or drugs. Navigation, record importing, and authentication may be effectively performed the use of the touch interface, improving the overall user experience.
6. Offline Authentication Capabilities:
In situations where net connectivity can be intermittent, sure UDIN cellular packages or platforms offer offline authentication abilities. Professionals can initiate the authentication process without an internet connection, and the device syncs the records as soon as connectivity is restored.
UDIN Login and Digital Signatures
In this section, we explore the synergistic dating between UDIN login and digital signatures.
1. Comprehensive Document Authentication:
UDIN and digital signatures together provide a comprehensive answer for report authentication. While UDIN guarantees a unique identifier for each record, virtual signatures upload an extra layer of protection through verifying the authenticity of the signer, developing a sturdy system for making sure file integrity.
2. Dual Authentication Assurance:
The mixture of UDIN and digital signatures offers dual assurance to stakeholders concerning the legitimacy of a report. UDIN provides a unique identifier that may be independently demonstrated, at the same time as a virtual signature authenticates the origin and integrity of the record, reinforcing confidence in the record’s credibility.
3. Enhanced Security Measures:
Digital signatures, frequently primarily based on cryptographic methods, offer superior safety features. The use of public and private key pairs ensures that handiest the authorized signatory can create a legitimate digital signature, adding a further layer of safety towards unauthorized alterations or forgeries.
4. Tamper-Evident Documents:
When UDIN and digital signatures are employed collectively, files come to be inherently tamper-evident. Any try to modify the content of the file or control the signature is detectable, ensuring that the record’s integrity remains intact in the course of its lifecycle.
5. Regulatory Compliance Alignment:
Many regulatory bodies emphasize the use of each UDIN and digital signatures for specific file types. By incorporating each elements into file authentication practices, professionals align with regulatory necessities, making sure compliance and mitigating felony risks.
6. User-Friendly Integration:
Modern systems regularly combine UDIN and digital signature functionalities seamlessly, supplying a person-friendly enjoy. Professionals can perform UDIN login and virtual signature methods within the identical workflow, minimizing complexity and streamlining record authentication techniques.
Frequently Asked Questions (FAQs)
A1: UDIN stands for Unique Document Identification Number. It’s a completely unique identifier assigned to professional documents, improving their authenticity and presenting traceability. Professionals use UDIN to illustrate the integrity in their work and comply with regulatory requirements.
A2: To sign up for UDIN login, go to the legit UDIN portal, navigate to the registration segment, and offer necessary personal and expert information. Create a stable password, undergo any required verification steps, and receive the phrases and situations to finish the registration.
A3: Yes, UDIN offers cell get right of entry to, allowing professionals to authenticate files anytime, everywhere. Ensure you have got a secure net connection, and use the cellular-pleasant interface for a continuing experience.
A4: If you forget about your UDIN login password, click at the “Forgot Password” link on the login page. Follow the instructions to reset your password, regularly regarding a reset link despatched via e mail or a verification code to your registered mobile quantity.
A5: UDIN and virtual signatures paintings synergistically to decorate record authentication. While UDIN offers a completely unique identifier for each document, virtual signatures authenticate the foundation and integrity of the document, offering dual guarantee of its legitimacy.




















