In the dynamic panorama of the virtual era, where records is a treasured asset, the security of touchy statistics is paramount for any organisation. A essential factor of this protection framework lies in the implementation of sturdy staff login systems. In this complete guide, we are able to resolve the intricacies of team of Staff login structures, emphasizing their pivotal function in fortifying organizational defenses and optimizing operational performance.
- Understanding the Importance of Robust Staff Login Systems
- Key Components of a Secure Staff Login System
- Choosing the Right Authentication Methods for Your Staff Login System
- Best Practices for Creating Strong Password Staff Login
- Implementing Two-Factor Authentication Staff Login
- Addressing Common Staff Login Challenges and Solutions
- The Role of Single Sign-ON in Simplifying Staff Login Processes
- Staff Training and Awareness for Secure Staff Login
- Frequently Asked Questions (FAQs)

Introduction
- In an age in which cyber threats loom huge, knowledge the importance of a steady personnel login gadget is the first step in the direction of fortifying your company’s virtual infrastructure. This guide will delve into the multifaceted advantages of such systems, shedding mild on how they not simplest guard touchy information but also contribute to the seamless functioning of day-to-day operations.
- The journey begins with a better study the important thing additives that constitute a steady personnel login machine. From encryption protocols to multi-thing authentication, every element plays a essential position in growing a resilient protection against unauthorized get right of entry to. Staff Login By understanding these additives, groups can tailor their login structures to meet the specific desires of their operations.
Understanding the Importance of Robust Staff Login Systems
These systems serve as the primary line of defense, protective touchy organizational facts from unauthorized get right of entry to and potential security breaches. In this phase, we can delve into the significance of having a steady body of workers login device and how it forms the bedrock of a resilient cybersecurity infrastructure.
1.1 Defending Against Unauthorized Access
- At the center of any company’s protection framework is the need to defend in opposition to unauthorized get entry to to touchy facts. Robust body of Staff login structures act because the gatekeepers, making sure that most effective authorized personnel can benefit access to vital structures, databases, and packages. This now not most effective protects the corporation’s proprietary facts however additionally safeguards the confidentiality of consumer records, economic facts, and different challenge-critical assets.
1.2 Mitigating the Risk of Data Breaches
- Data breaches will have excessive consequences, starting from monetary losses to reputational damage. A properly-designed team of workers login gadget drastically mitigates the danger of facts breaches by way of imposing state-of-the-art authentication protocols and encryption measures. This proactive technique allows agencies stay one step in advance of cybercriminals who continually are searching for to exploit vulnerabilities in login systems.
1.3 Safeguarding Employee Credentials
- Employees are the lifeblood of any organisation, and their credentials are valuable belongings that should be protected. A robust team of Staff Login machine ensures the confidentiality of worker usernames and passwords, preventing unauthorized individuals from getting access to touchy personnel records. This no longer only protects employees from identification theft however also reinforces a lifestyle of trust in the business enterprise.
1.4 Ensuring Compliance with Regulatory Standards
- In an era of growing facts privacy rules, compliance is not optionally available
it’s a need. Robust personnel login systems play a vital position in ensuring that companies adhere to industry-particular and regional regulatory standards. Whether it is GDPR in Europe, HIPAA in healthcare, or other zone-specific guidelines, a steady login machine helps businesses meet compliance requirements and keep away from criminal repercussions.
1.5 Enhancing Operational Efficiency
- Security and efficiency want no longer be collectively special. A well-designed staff login device streamlines get admission to to essential systems and programs, allowing legal employees to navigate seamlessly thru their daily obligations. This stability between security and efficiency contributes to a effective person revel in, fostering productivity in the corporation.
Key Components of a Secure Staff Login System
2.1 Authentication Protocols
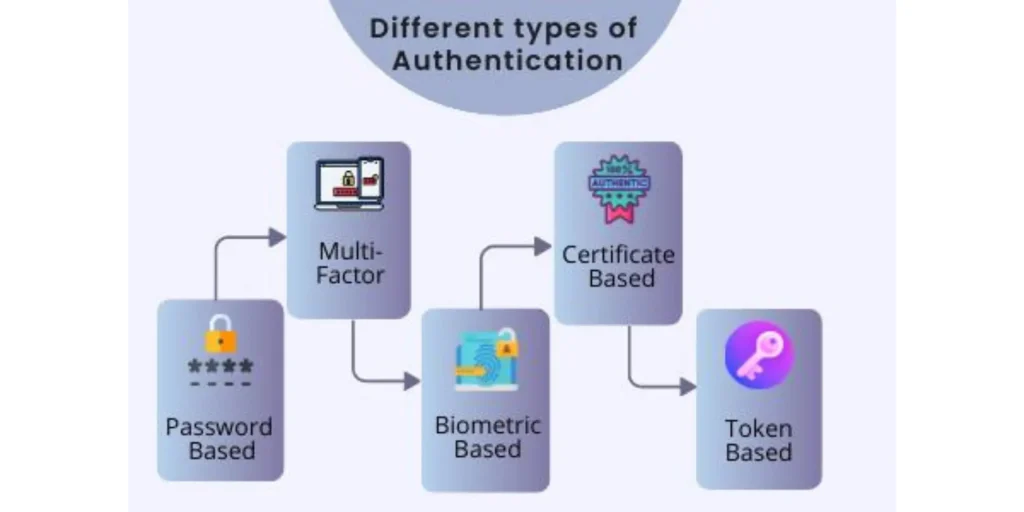
- Authentication serves because the first line of protection in a staff login device. Different authentication protocols, together with username and password combinations, biometrics, clever cards, or token-primarily based systems, confirm the identity of customers attempting to get entry to the gadget. The preference of authentication approach must align with the agency’s safety necessities and the character of the information being covered.
2.2 Encryption Mechanisms
- Once a consumer’s identification is confirmed, the subsequent crucial step is to secure the transmission of data between the consumer’s device and the server. Encryption mechanisms, which includes Secure Sockets Layer (SSL) or Transport Layer Security (TLS), ensure that facts is encrypted during transit, stopping unauthorized interception and eavesdropping. This layer of protection is mainly vital when sensitive records is transmitted over networks.
2.3 Multi-Factor Authentication (MFA)
- Multi-Factor Authentication adds an additional layer of protection by using requiring users to provide multiple varieties of identification before gaining get entry to. This may want to encompass a mixture of something the person knows (password), some thing the person has (smart card or token), or some thing the user is (biometric data). MFA significantly strengthens the authentication method, Staff Login lowering the likelihood of unauthorized get admission to despite the fact that one thing is compromised.
2.4 Access Controls and Permissions
- Granular access controls and permissions outline what assets and information person users or agencies can access in the system. By enforcing least privilege standards, companies restrict user get admission to to best the data essential for their roles. This minimizes the danger of unintended records exposure or intentional misuse.
2.5 Session Management
- Effective consultation management is important for retaining protection for the duration of a person’s interaction with the system. This consists of measures along with consultation timeouts, which routinely log customers out after a length of inactiveness, and steady session storage practices. Proper session control prevents unauthorized get right of entry to in case a consumer forgets to log out or if a tool is left unattended.
2.6 Password Policies
- Passwords stay a essential detail of consumer authentication. Implementing strong password rules, together with necessities for complexity, duration, and normal updates, adds a further layer of protection against unauthorized get right of entry to. Educating users approximately password first-class practices is similarly essential in developing a safety-conscious tradition in the business enterprise.
2.7 Account Lockout Mechanisms
- To thwart brute pressure attacks, account lockout mechanisms routinely lock person money owed after a sure wide variety of unsuccessful login tries. This prevents malicious actors from again and again attempting to benefit get right of entry to via trial and errors. Careful attention of lockout thresholds is essential to balance safety with capability consumer inconvenience.
2.8 Logging and Auditing
- Comprehensive logging and auditing mechanisms music user sports in the system. These logs may be precious for identifying suspicious conduct, investigating security incidents, and keeping compliance with regulatory requirements. Regularly reviewing and studying logs is a proactive degree in identifying and mitigating capacity security threats.
Choosing the Right Authentication Methods for Your Staff Login System
Selecting the correct authentication strategies for your group of workers login system is a pivotal selection that immediately impacts the gadget’s protection, usability, Staff Login and average effectiveness. In this section, we will discover various authentication techniques, considering their strengths, weaknesses, and suitability for distinctive organizational contexts.
3.1 Password-Based Authentication
- Password-based totally authentication is the most not unusual and conventional approach. Users offer a unique combination of a username and password to get entry to the gadget. While easy and acquainted, this method is at risk of vulnerabilities which include susceptible passwords, password reuse, and the hazard of brute-force assaults. Best practices for password-based authentication consist of enforcing strong password regulations, implementing account lockout mechanisms, and teaching users on stable password practices.
3.2 Biometric Authentication
- Biometric authentication is based on unique physiological or behavioral traits, which include fingerprints, facial recognition, iris scans, or voice reputation, to verify a consumer’s identity. Biometrics provide a high degree of protection as they’re difficult to forge, but they’ll pose privacy issues and are concern to ability false positives or negatives. Implementing biometric authentication requires careful consideration of consumer consent, criminal implications, and the supply of dependable biometric scanners.
3.4 Multi-Factor Authentication (MFA)
- Multi-Factor Authentication (MFA) combines or more authentication strategies to beautify security. Staff Login For example, a consumer might also need to provide a password (something they know) and use a fingerprint test (something they’re). MFA significantly reduces the danger of unauthorized get admission to, even if one authentication thing is compromised. Organizations need to carefully select the aggregate of things primarily based on their protection requirements and consumer convenience.
3.5 Single Sign-On (SSO)
- Single Sign-On (SSO) lets in customers to log in once and get entry to a couple of structures or programs with out re-getting into credentials. While SSO enhances user convenience and productivity, it comes with safety issues. A compromised SSO credential should potentially supply access to multiple structures, making it crucial to put in force sturdy authentication measures and robust session management.
3.6 Time-Based One-Time Passwords (TOTP) and SMS Authentication
- Time-Based One-Time Passwords (TOTP) generated by way of authenticator apps and SMS authentication contain sending one-time codes to customers’ cell devices. These strategies offer a further layer of protection, but SMS-primarily based authentication is vulnerable to SIM swapping assaults. TOTP is more stable but requires customers to have get entry to to a like minded authenticator app.
Best Practices for Creating Strong Password Staff Login
Implementing and implementing best practices for password creation is vital in fortifying the security of your personnel login machine. Here are a few encouraged fine practices:
1. Length and Complexity:
- Longer is Better: Encourage users to create passwords with a minimum period of 12 characters. Longer passwords provide an additional layer of safety.
- Mix Character Types: Include a aggregate of uppercase and lowercase letters, numbers, and unique characters. This complexity makes passwords greater proof against brute-pressure attacks.
2. Avoid Common Password Pitfalls:
- No Personal Information: Discourage the usage of effortlessly guessable data consisting of names, birthdays, or commonplace phrases. Hackers regularly use these information in targeted attacks.
- Avoid Dictionary Words: Dictionary assaults contain trying common phrases in numerous combos. Staff Login Strong passwords need to not contain recognizable words.
- No Sequential or Repeated Characters: Eliminate sequences like “12345” or repeated characters like “aaaa.” These patterns are without problems guessed.
3. Regular Password Updates:
- Enforce Regular Changes: Set guidelines that require customers to trade their passwords at normal intervals. This practice reduces the threat of compromised credentials.
- Avoid Reuse: Discourage the reuse of passwords throughout distinctive money owed. If one account is compromised, using the identical password someplace else exposes extra vulnerabilities.
4. Password Management:
- Use a Password Manager: Encourage the use of password control tools. These tools generate and shop complicated passwords, doing away with the need for users to remember multiple passwords.
- Two-Factor Authentication (2FA): Implement 2FA to feature a further layer of security. Even if passwords are compromised, Staff Login a further authentication component is needed for get right of entry to.
5. Education and Awareness:
- User Training: Provide everyday education periods to educate customers approximately the significance of sturdy passwords and the capability risks related to weak ones.
- Phishing Awareness: Educate customers approximately phishing attacks that try to trick them into revealing passwords. Remind them not to proportion passwords thru electronic mail or on suspicious websites.
6. Account Lockout Policies:
- Implement Lockout Mechanisms: Set up account lockout regulations that temporarily lock user bills after a special variety of unsuccessful login tries. This facilitates save you brute-pressure assaults.
- Notify Users of Lockouts: Inform users when their bills are locked and provide steerage on unlocking strategies. Staff Login This allows customers take corrective moves promptly.
7. Encourage Passphrases:
- Passphrases Over Passwords: Consider selling the usage of passphrases—a series of random phrases or a sentence. Passphrases are regularly simpler for users to recollect and can be just as steady as complex passwords.
- Spaces and Special Characters: Allow the usage of areas and special characters in passphrases to increase complexity.
8. Regular Security Audits:
- Conduct Password Audits: Periodically evaluation and audit passwords to perceive weak or compromised ones. Prompt customers to replace their passwords if important.
- Monitor for Anomalies: Implement monitoring equipment to detect uncommon login patterns or suspicious sports, indicating potential safety threats.
Implementing Two-Factor Authentication Staff Login
Implementing Two-Factor Authentication (2FA) on your personnel login gadget is a effective strategy to decorate protection by means of including an extra layer of verification beyond conventional passwords. This section will manual you thru the step-by means of-step process of implementing 2FA correctly:
1. Choose the Right 2FA Method:
- Time-Based One-Time Passwords (TOTP): TOTP generates a completely unique, time-touchy code on a consumer’s mobile device the use of an authenticator app like Google Authenticator or Authy.
- SMS or Email Codes: Users acquire a one-time code via SMS or email that they should input in conjunction with their password throughout login.
- Biometric Verification: Utilize fingerprint scans, facial recognition, or other biometric data as the second authentication component.
- Hardware Tokens: Issue bodily devices (e.G., USB tokens) that generate or store authentication codes.
2. Integrate 2FA into the Authentication Workflow:
- Adapt the Login Interface: Modify your login interface to activate customers for the second thing once they enter their password. Clearly communicate the want for 2FA in the course of the Staff Login system.
- Backend Integration: Integrate the chosen 2FA approach into your authentication backend. This may additionally contain connecting with 1/3-celebration authentication offerings or imposing custom answers.
3. User Enrollment and Education:
- User Registration: Implement a person registration method that publications users via the 2FA setup. Provide clean commands and walkthroughs for each 2FA approach.
- Educational Resources: Offer documentation, tutorials, or movies explaining the significance of 2FA and a way to set it up. Emphasize the brought protection it offers.
4. Support Multiple 2FA Methods:
- Flexibility for Users: Allow customers to select from extraordinary 2FA methods based totally on their choices and device talents. Providing alternatives increases person adoption.
- Fallback Mechanism: Implement a stable fallback mechanism for situations wherein the primary 2FA technique is unavailable, ensuring continuous get right of entry to.
5. Secure 2FA Codes:
- Encryption: Ensure that 2FA codes are transmitted and stored securely using encryption protocols. This prevents interception or unauthorized get admission to to the codes.
- Expiration Policies: Implement policies that define the validity length of 2FA codes to lessen the risk associated with code reuse.
6. Monitor and Audit 2FA Events:
- Logging: Implement comprehensive logging for 2FA activities. Record successful and unsuccessful attempts, Staff Login including information like timestamps, person IDs, and authentication methods used.
- Monitoring Tools: Utilize monitoring tools to locate unusual styles or multiple failed 2FA attempts, which can also indicate a security risk.
7. Regularly Update 2FA Policies:
- Stay Informed: Keep abreast of advancements in 2FA technology and security standards. Update your 2FA guidelines and methods as a result to cope with rising threats.
- User Communication: Inform users of any changes to 2FA policies, and provide steerage on updating their settings if important.
8. Test and QA:
- Testing Environment: Implement 2FA in a trying out environment earlier than rolling it out to manufacturing. This enables perceive and address any problems or compatibility concerns.
- User Feedback: Collect comments from users during the testing segment to understand their enjoy and address any usability worries.
Addressing Common Staff Login Challenges and Solutions
Staff login systems frequently come across various demanding situations which could impact user enjoy, safety, and ordinary device efficiency. In this section, we’ll cope with common staff login demanding situations and provide sensible solutions to mitigate these issues:
1. Forgotten Passwords:
Challenge: Users regularly forget their passwords, main to account lockouts and productiveness disruptions.
Solution:
- Implement self-service password reset mechanisms.
- Utilize protection questions or password guidelines for user verification.
- Encourage the usage of password managers to store and retrieve passwords securely.
2. Account Lockouts:
Challenge: Excessive failed login tries can result in account lockouts, causing frustration for users.
Solution:
- Set up account lockout rules with reasonable thresholds.
- Implement transient lockouts to deter brute-force assaults.
- Provide users with clear instructions on unlocking their money owed.
3. Phishing Attacks:
Challenge: Users may fall sufferer to phishing attacks that trick them into revealing login credentials.
Solution:
- Conduct normal phishing consciousness schooling for team of workers.
- Implement e mail filtering to come across and block phishing attempts.
- Use multi-element authentication (MFA) to add an extra layer of security.
4. Slow Authentication Processes:
Challenge: Cumbersome authentication procedures can cause delays in getting access Staff Login to critical systems.
Solution:
- Optimize backend structures to lessen authentication processing instances.
- Implement caching mechanisms for often accessed statistics.
- Consider adaptive authentication to streamline the method based totally on contextual factors.
5. Inconsistent User Experience:
Challenge: Users may also revel in inconsistencies in the login process across one of a kind structures or packages.
Solution:
- Implement Single Sign-On (SSO) to provide a unified login revel in.
- Standardize authentication techniques and interfaces across applications.
- Ensure clear verbal exchange approximately the authentication system to customers.
6. Mobile Access Challenges:
Challenge: Users getting access to structures from mobile gadgets might also face compatibility problems or a less person-pleasant interface.
Solution:
- Implement responsive layout for cellular-friendly login interfaces.
- Offer a committed cellular app for seamless access.
- Ensure that multi-thing authentication techniques are mobile-friendly.
7. Unauthorized Access Attempts:
Challenge: Malicious actors may additionally try to advantage unauthorized get entry to by means of exploiting vulnerabilities.
Solution:
- Implement intrusion detection and prevention structures.
- Regularly audit and reveal login sports for Staff Login uncommon styles.
- Enforce sturdy authentication strategies and train users approximately safety exceptional practices.
8. Integration Challenges with Third-Party Systems:
Challenge: Integrating login structures with third-birthday party applications can also pose compatibility and statistics synchronization demanding situations.
Solution:
- Use standardized protocols (e.G., OAuth, SAML) for seamless integration.
- Regularly update integrations to align with evolving security standards.
- Work carefully with 0.33-birthday party carriers to address compatibility problems.
The Role of Single Sign-ON in Simplifying Staff Login Processes
Staff Login Processes
- In the ever-evolving landscape of digital workplaces, groups seek innovative answers to streamline operations and enhance consumer revel in. Single Sign-On (SSO) has emerged as a effective tool, simplifying body of workers login methods and contributing to accelerated performance and security. In this phase, we discover the key components of SSO and the way it transforms the login enjoy for staff members.
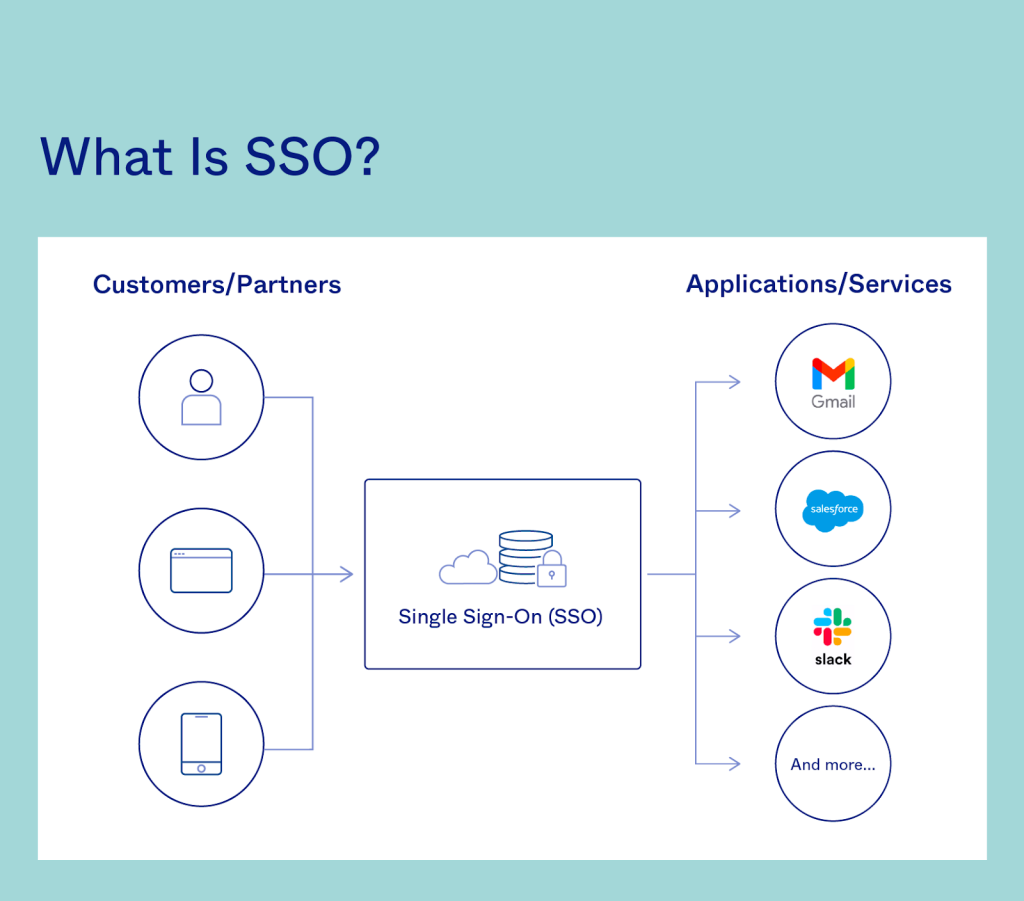
1. Understanding Single Sign-On (SSO):
- Single Sign-On is an authentication procedure that lets in customers to get right of entry to multiple applications and systems with a single set of credentials. Instead of requiring customers to log in separately for every software, SSO authenticates the consumer once, granting them get admission to to various linked structures without the want for repeated Staff Login.
2. Streamlining User Access:
- One of the primary advantages of SSO is the elimination of the need for users to recall and input a couple of units of credentials. With a unmarried login, group of workers participants can seamlessly get admission to numerous programs, databases, and structures, lowering the friction associated with multiple logins during the workday.
3. Enhanced User Experience:
- SSO significantly complements the consumer enjoy via simplifying the login technique. Users recognize the convenience of getting access to all legal systems with a single login, main to extended productiveness and a greater positive normal experience.
4. Improved Security:
- While SSO simplifies the login manner, it would not compromise protection. In fact, it is able to decorate security with the aid of implementing sturdy authentication for the preliminary Staff Login. Multi-Factor Authentication (MFA) may be seamlessly incorporated with SSO, adding a further layer of safety to make sure that simplest authorized customers advantage get admission to to the whole suite of applications.
5. Centralized User Management:
- SSO permits for centralized user control, enabling administrators to control get entry to and permissions from a single factor. When a body of workers member’s function or get entry to necessities exchange, directors can update permissions centrally, ensuring consistency and reducing the chance of oversights in get entry to management.
6. Time and Cost Savings:
- By decreasing the time spent on coming into and handling more than one sets of credentials, SSO leads to time financial savings for each users and IT administrators. This interprets into extended efficiency and, in the long run, fee financial savings for the organisation.
7. Seamless Integration with Enterprise Applications:
- SSO can seamlessly combine with a wide range of organization packages, such as cloud-primarily based offerings, electronic mail systems, collaboration equipment, and business software program. This adaptability makes it a flexible solution for organizations with numerous generation stacks.
8. Mobile Accessibility:
- With the growing incidence of mobile work environments, SSO allows easy and steady get right of entry to to applications from various devices. Whether personnel participants are operating from the office, remotely, or at the pass, SSO presents a constant and stable login enjoy.
Staff Training and Awareness for Secure Staff Login
In this segment, we discover the importance of body of workers schooling and cognizance for steady workforce login and description key strategies for creating a cyber-savvy place of job.
1. Understanding the Human Element in Cybersecurity:
- Despite superior technological solutions, human blunders stays a leading purpose of protection breaches. Recognizing the human element in cybersecurity is the first step towards constructing a sturdy defense strategy.
2. Importance of Staff Training:
- Effective workforce training is a cornerstone of a stable personnel login system. It empowers personnel with the understanding and capabilities had to navigate the virtual panorama securely. Training projects need to cover a range of subjects, together with password nice practices, spotting phishing tries, and understanding the importance of secure login processes.
3. Key Components of Staff Training:
- Password Security: Educate body of workers at the significance of strong and particular passwords. Provide pointers on creating complicated passwords and the risks related to password reuse.
- Multi-Factor Authentication (MFA): Explain the importance of MFA in including an additional layer of safety. Train personnel on how to installation and use MFA for stable logins.
- Phishing Awareness: Conduct ordinary schooling classes on spotting phishing emails, websites, and social engineering methods. Equip workforce with the abilities to pick out capacity threats and record them directly.
- Secure Login Practices: Demonstrate the proper techniques for logging in securely, consisting of verifying website URLs, using steady networks, and being cautious approximately sharing login credentials.
- Mobile Security: Provide recommendations for steady login practices on mobile devices, emphasizing the significance of tool protection, app permissions, and the usage of stable networks.
4. Continuous Awareness Campaigns:
- Regular Updates: Keep team of workers knowledgeable approximately evolving cybersecurity threats and high-quality practices via everyday updates. Highlight actual-global examples and case research to illustrate capability dangers.
- Internal Communication: Establish clear verbal exchange channels for disseminating protection-related data. Use email, intranet, and different internal structures to percentage pointers, alerts, and reminders.
5. Simulated Security Exercises:
- Phishing Simulations: Conduct simulated phishing sporting activities to test group of workers members’ capacity to apprehend and respond to phishing tries. Provide comments and reinforcement based totally on the effects.
- Tabletop Exercises: Organize tabletop physical activities to simulate safety incidents. This allows staff recognize their roles and duties in responding to capacity threats.
6. Collaboration with IT and Security Teams:
- Open Communication: Foster a subculture of open communique among personnel, IT groups, and cybersecurity professionals. Encourage employees to file any suspicious sports directly.
- Responsive Support:Ensure that there is a responsive guide system in vicinity for staff to are searching for assistance or report security issues. Promptly address any stated incidents or potential threats.
7. Tailoring Training to Roles and Responsibilities:
- Role-Specific Training: Customize training applications primarily based on the specific roles and responsibilities of body of workers members. Tailoring content ensures relevance and applicability to their daily tasks.
- Executive Training: Provide specialised education for executives and high-profile objectives who may be targeted in state-of-the-art attacks. Emphasize the importance of main through instance in practising stable login conduct.
Frequently Asked Questions (FAQs)
A1: Artificial Intelligence (AI) refers to the simulation of human intelligence in machines which might be programmed to suppose and study. It encompasses numerous technologies like machine learning, natural language processing, and pc imaginative and prescient.
A2: Machine getting to know involves algorithms that permit computer systems to learn from information. These algorithms enable structures to become aware of patterns, make selections, and improve their overall performance over time with out being explicitly programmed.
A3: Machine getting to know is a broader idea that includes various strategies, even as deep gaining knowledge of is a subset of machine mastering that makes a speciality of neural networks with more than one layers (deep neural networks) to model and remedy complex problems.




















