In the opening chapters, we can delve into the essential components of Safe Shop, highlighting its pivotal position within the e-trade atmosphere. Understanding the importance of a stable platform sets the degree for groups to construct trust with their clients. A certain exploration of the Safe Shop login method, entire with step-by way of-step commands, follows, ensuring that customers can effects get right of entry to their debts while merchants manipulate their operations quite simply.
- Understanding Safe Shop Login and Its Importance in E-commerce
- Navigating the Safe Shop Login Page
- Security Features of Safe Shop Login: Protecting Your Business
- Troubleshooting Common Safe Shop Login Issues
- Safe Shop Login Best Practices: Enhancing Security
- Integrating Safe Shop Login with Third-Party Platforms
- Optimizing User Experience: Safe Shop Login on Mobile Devices
- Safe Shop Login Analytics: Leveraging Data for Business Growth
- Frequently Asked Questions (FAQs)
Introduction
- Security isn’t always a one-length-fits-all idea, and in the virtual realm, wherein threats constantly evolve, having strong safety functions is imperative. Therefore, we are able to scrutinize the safety measures embedded inside Safe Shop, from encryption protocols to 2-thing authentication, offering a comprehensive evaluate of how the platform protects each businesses and their purchasers.
- While safety is a priority, troubleshooting is an inevitable factor of online systems. Our manual includes a dedicated phase to deal with common Safe Shop login issues, equipping customers and administrators with the expertise to swiftly remedy any hurdles and maintain a continuing on line enjoy.
Understanding Safe Shop Login and Its Importance in E-commerce
The Authentication Process:
- The Safe Shop login procedure entails the verification of user credentials, usually through a combination of usernames and passwords. This initial step acts as a gatekeeper, allowing handiest legal individuals to get admission to the platform. This authentication technique is essential in preventing unauthorized get right of entry to and shielding user accounts from ability threats.
Importance in E-trade:
Secure Transactions:
- In the arena of online enterprise, wherein economic transactions arise often, the stable login furnished with the aid of Safe Shop is instrumental. It ensures that fee records, private info, and different sensitive data are covered from malicious actors searching for unauthorized get admission to.
Builds Customer Trust:
- Trust is the cornerstone of a success e-commerce ventures. Safe Shop login instills self assurance in clients, assuring them that their facts is treated with the utmost care. This agree with is a effective driving force for patron loyalty and repeat enterprise.
Prevents Fraudulent Activities:
- E-commerce platforms are prone to various styles of fraud, consisting of identification robbery and account takeovers. Safe Shop’s robust authentication measures act as a deterrent, thwarting capability cyber threats and safeguarding both groups and their purchasers.
Protects Business Reputation:
- A security breach can have severe repercussions for an e-commerce business, leading to economic losses and damage to reputation. Safe Shop mitigates those dangers by means of fortifying the login method, ensuring that sensitive business records remains exclusive.
Compliance with Industry Standards:
- Adherence to enterprise rules and information safety requirements is non-negotiable. Safe Shop aligns with these requirements, offering agencies with a steady framework that complies with felony necessities, thereby heading off ability legal pitfalls.
In conclusion, information Safe Shop login is paramount for corporations searching for to thrive within the aggressive panorama of e-commerce. Beyond being a mere gateway to a platform, Safe Shop is a guardian of consider, ensuring secure transactions, preventing fraud, and safeguarding the popularity of organizations.
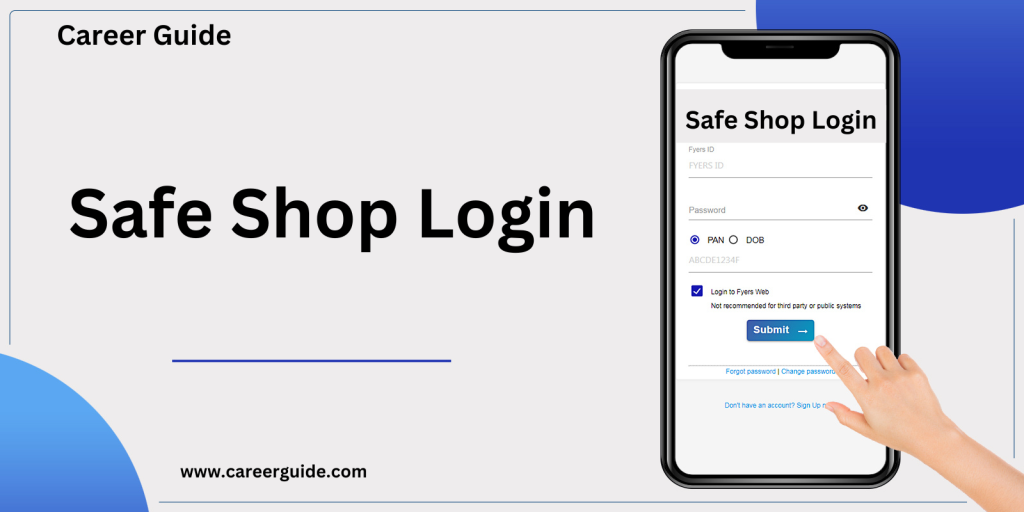
Navigating the Safe Shop Login Page
Navigating this portal correctly is essential for both users and merchants alike. In this segment, we will embark on a step-through-step journey, unraveling the intricacies of the Safe Shop login web page and offering users with the know-how to get right of entry to their bills seamlessly.
1-Step: Accessing the Safe Shop Login Page
- Begin by means of navigating to the legitimate Safe Shop internet site. The login page is typically prominently featured, either as a critical element on the homepage or thru a committed login section.
2-Step: Entering User Credentials
- Once at the Safe Shop login page, customers are precipitated to enter their credentials. This normally involves supplying a aggregate of a username and a password. It’s crucial to enter this data correctly, as it serves because the primary manner of authentication.
3-Step: Two-Factor Authentication (Optional)
- Many stable structures, which include Safe Shop, offer an extra layer of security via -factor authentication (2FA). If enabled, customers may be required to enter a secondary code sent to their registered cellular tool or email address. This extra step considerably complements the safety of the login technique.
4-Step: Password Recovery and Assistance
- In the event of forgotten passwords or other login problems, Safe Shop usually offers a “Forgot Password” or “Need Help?” option. Users can observe the activates to reset their passwords or seek assistance from Safe Shop support offerings.
5-Step: Captcha Verification
- To prevent computerized bots from gaining unauthorized access, Safe Shop frequently employs captcha verification. Users may be required to finish a simple mission, inclusive of figuring out objects in pix, to show that they are human.
6-Step: Secure Connection Verification
- Before proceeding, make certain that the connection to the Safe Shop login page is stable. Look for “https://” in the URL, indicating that the relationship is encrypted, and facts transmission is secure.
7-Step: Successful Login
- Upon successful authentication, customers are granted access to their Safe Shop bills. This marks the crowning glory of the login process, and users can now explore the functions and functionalities of the platform.
Security Features of Safe Shop Login: Protecting Your Business
In this segment, we’re going to discover the security functions of Safe Shop login, unraveling the layers of protection that make a contribution to a secure and straightforward on line environment.
1. Encryption Protocols:
- At the middle of Safe Shop’s protection infrastructure lies superior encryption protocols. These cryptographic techniques ensure that every one information transmitted between the user’s device and Safe Shop’s servers stays exclusive and stable. The use of protocols like HTTPS establishes a stable connection, defensive against capacity eavesdropping and data breaches.
2. Two-Factor Authentication (2FA):
- Two-Factor Authentication adds an extra layer of security to the login system. In addition to the conventional username and password, customers are required to provide a secondary shape of verification. This can take the shape of a temporary code sent to a registered cell tool or e-mail address. 2FA extensively reduces the danger of unauthorized get right of entry to, despite the fact that login credentials are compromised.
3. Biometric Authentication:
- Safe Shop is at the leading edge of adopting biometric authentication strategies. Leveraging fingerprint scans, facial popularity, or other biometric markers adds an additional measurement of safety. Biometric facts is particular to each consumer, making it an powerful method of ensuring that best legal people gain get entry to to the platform.
4. Account Lockout Policies:
- To thwart brute-pressure assaults, Safe Shop employs account lockout regulations. After a positive variety of unsuccessful login tries, the account is temporarily locked, preventing in addition unauthorized get right of entry to attempts. This proactive measure adds a further layer of defense towards malicious actors attempting to benefit entry via repeated login attempts.
5. Device Recognition and Management:
- Safe Shop includes tool popularity and control capabilities to decorate safety. Users can sign in and manage the gadgets they use to get admission to their accounts. Any try to log in from an unrecognized tool might also cause extra protection tests or notifications to the account proprietor, imparting an early warning gadget for capability unauthorized get right of entry to.
6. Session Management and Timeout Controls:
- Safe Shop implements strong session management controls to monitor and manipulate consumer periods. Automatic logout after a duration of state of being inactive facilitates save you unauthorized access in case a consumer forgets to sign off. This characteristic is mainly essential in shared or public computing environments.
7. Regular Security Audits and Updates:
- The virtual panorama is dynamic, and threats continuously evolve. Safe Shop conducts regular protection audits to pick out and cope with vulnerabilities. Timely updates and patches are deployed to ensure that the platform remains resilient against rising safety dangers.
Troubleshooting Common Safe Shop Login Issues
In this segment, we’ll delve into the security features of Safe Shop login, unraveling the layers of safety that make contributions to a stable and sincere on line environment.
1. Encryption Protocols:
- At the core of Safe Shop’s protection infrastructure lies superior encryption protocols. These cryptographic strategies make sure that all records transmitted among the user’s device and Safe Shop’s servers stays exclusive and stable. The use of protocols like HTTPS establishes a steady connection, shielding against capacity eavesdropping and information breaches.
2. Two-Factor Authentication (2FA):
- Two-Factor Authentication provides a further layer of security to the login process. In addition to the traditional username and password, users are required to offer a secondary shape of verification. This can take the shape of a transient code despatched to a registered mobile tool or e-mail cope with. 2FA drastically reduces the danger of unauthorized access, although login credentials are compromised.
3. Biometric Authentication:
- Safe Shop is at the forefront of adopting biometric authentication techniques. Leveraging fingerprint scans, facial popularity, or other biometric markers provides an additional dimension of protection. Biometric records is unique to each consumer, making it an powerful manner of making sure that handiest authorized individuals gain get admission to to the platform.
4. Account Lockout Policies:
- To thwart brute-pressure attacks, Safe Shop employs account lockout regulations. After a positive variety of unsuccessful login tries, the account is temporarily locked, preventing in addition unauthorized access attempts. This proactive measure adds a further layer of protection in opposition to malicious actors attempting to gain entry through repeated login tries.
5. Device Recognition and Management:
- Safe Shop contains tool reputation and control capabilities to enhance safety. Users can sign up and control the devices they use to get admission to their money owed. Any attempt to log in from an unrecognized tool may additionally trigger additional security assessments or notifications to the account proprietor, presenting an early warning device for capacity unauthorized access.
6. Session Management and Timeout Controls:
- Safe Shop implements strong consultation control controls to reveal and control person periods. Automatic logout after a length of state of being inactive allows prevent unauthorized get right of entry to in case a user forgets to log off. This function is specially important in shared or public computing environments.
7. Regular Security Audits and Updates:
- The digital landscape is dynamic, and threats continuously evolve. Safe Shop conducts normal protection audits to perceive and deal with vulnerabilities. Timely updates and patches are deployed to ensure that the platform stays resilient against rising protection dangers.
Safe Shop Login Best Practices: Enhancing Security
In this segment, we’re going to explore nice practices for Safe Shop login, supplying both administrators and users with suggestions to enhance the security of their online interactions.
1. Create Strong and Unique Passwords:
- The foundation of steady login lies inside the power of passwords. Encourage users to create passwords that are each robust and precise. A aggregate of uppercase and lowercase letters, numbers, and special characters contributes to a sturdy password. Avoid without problems guessable statistics along with birthdays or common phrases.
2. Enable Two-Factor Authentication (2FA):
- Two-Factor Authentication adds an extra layer of protection by way of requiring customers to offer a secondary form of verification further to their passwords. Enable 2FA to decorate the authentication technique, reducing the chance of unauthorized get right of entry to, despite the fact that login credentials are compromised.
3. Regularly Update Passwords:
- Periodic password adjustments are a good exercise to mitigate the threat of unauthorized get admission to. Encourage customers to replace their passwords often, and remember enforcing guidelines that spark off customers to change their passwords at described periods.
4. Educate Users on Phishing Awareness:
- Phishing assaults regularly goal login credentials through deceptive emails or web sites. Educate users about the signs and symptoms of phishing and emphasize the significance of verifying the authenticity of emails or links earlier than supplying any login facts.
5. Monitor Account Activity:
- Regularly reveal account interest to hit upon any suspicious or unauthorized get right of entry to. Safe Shop regularly presents customers with gear to check recent login records and active periods. Encourage customers to robotically check these logs for any anomalies.
6. Secure Devices and Networks:
- Emphasize the importance of the use of stable and trusted devices and networks whilst accessing Safe Shop. Public Wi-Fi networks can also pose safety risks, so users ought to keep away from accessing their debts on unsecured connections. Additionally, make certain that devices used to get entry to Safe Shop are protected with up-to-date safety features.
Integrating Safe Shop Login with Third-Party Platforms
In this section, we will discover the opportunities and benefits of integrating Safe Shop login with 0.33-celebration systems, supplying organizations a comprehensive understanding of ways this collaboration can make contributions to a cohesive and green online enterprise surroundings.
1. Payment Gateways Integration:
- One of the number one areas where Safe Shop login integration proves invaluable is within the realm of price gateways. Linking Safe Shop login with popular charge offerings streamlines the checkout manner for users, reducing friction and improving the overall shopping experience. This integration ensures that customers can seamlessly transition from surfing products to completing transactions without the need for multiple logins.
2. Customer Relationship Management (CRM) Systems:
- Integrating Safe Shop login with CRM structures permits organizations to consolidate consumer records and interactions. This unified technique enables a holistic view of customer behavior, preferences, and purchase history. As a end result, organizations can tailor their marketing strategies, customize consumer experiences, and foster more potent relationships with their customer base.
3. Inventory and Order Management Systems:
- Efficient stock and order management are crucial components of a success e-commerce operations. Integrating Safe Shop login with these systems facilitates real-time synchronization of facts. This guarantees that changes in product availability, order repute, and delivery statistics are seamlessly reflected, lowering the likelihood of mistakes and enhancing the accuracy of business operations.
4. Marketing and Analytics Platforms:
- Safe Shop login integration with advertising and analytics structures offers organizations with a complete view of user behavior and marketing campaign effectiveness. By connecting Safe Shop information with advertising and marketing analytics, companies can measure the effect of advertising efforts, tune conversion fees, and make information-driven choices to optimize their techniques.
5. Social Media Integration:
- Facilitate social media login alternatives via Safe Shop to enhance consumer comfort and extend the attain of your on line enterprise. Allowing customers to log in with their social media credentials no longer simplest simplifies the registration system but also presents agencies with extra information insights from users’ social profiles.
6. Content Management Systems (CMS):
- For organizations coping with a website or online shop, integrating Safe Shop login with content material control structures streamlines person authentication and get entry to manage. This integration guarantees that user bills are seamlessly controlled throughout exceptional sections of the website, offering a cohesive person experience.
Optimizing User Experience: Safe Shop Login on Mobile Devices
Safe Shop login on cell devices, ensuring a easy and steady enjoy for users on the pass.
1. Responsive Design:
- Adopt a responsive layout technique to make certain that the Safe Shop login web page adapts seamlessly to extraordinary display sizes and orientations. This guarantees that users having access to the platform from numerous mobile gadgets, inclusive of smartphones and capsules, revel in a visually appealing and person-friendly interface.
2. Touch-Friendly Interface:
- Design the Safe Shop login interface with contact-pleasant factors. Buttons, input fields, and navigation menus must be accurately sized to accommodate touch gestures. This ensures that users can engage with the login page effortlessly, reducing the possibilities of mistakes and improving average usability.
3. Simplified Login Process:
- Streamline the Safe Shop login system on cellular gadgets by means of minimizing the quantity of steps and input fields. Consider imposing features like social media login or biometric authentication to simplify the authentication procedure, making it quick and convenient for cellular users.
4. Mobile-Friendly Captcha:
- If captcha verification is necessary, make certain that the implementation is mobile-friendly. Opt for captcha solutions that are smooth to complete on smaller screens and do not impede the user revel in. Mobile-pleasant captchas make a contribution to a smoother login method for customers gaining access to Safe Shop on their smartphones.
5. Efficient Keyboard Input:
Optimize the keyboard input experience by using leveraging the correct input types for cellular devices. For instance, use the “email” enter kind for email addresses, which triggers the proper keyboard layout, making it less complicated for customers to go into their records accurately.
6. Clear Error Messages and Validation:
- Provide clean and concise blunders messages in case of login problems. Ensure that error messages are prominently displayed and easily understandable on mobile screens. Additionally, enforce actual-time validation to alert customers approximately any capability troubles with their login credentials earlier than they publish the form.
7. Progressive Web App (PWA) Features:
- Consider imposing Progressive Web App functions to beautify the general cell revel in. PWAs offer customers with the advantages of both net and local mobile packages, which include faster loading instances, offline competencies, and the capability to add the net app to the device’s domestic display.
Safe Shop Login Analytics: Leveraging Data for Business Growth
In this phase, we will explore how corporations can harness Safe Shop login analytics to their advantage and liberate the capacity for strategic choice-making.
1. User Behavior Analysis:
- Safe Shop login analytics allow agencies to track and analyze user conduct. By inspecting login patterns, groups can advantage insights into height utilization instances, frequency of logins, and preferred gadgets utilized by their customers. Understanding person conduct permits corporations to tailor their strategies to meet the desires of their target audience.
2. Conversion Rate Optimization:
- Analyzing login records in correlation with conversion charges presents businesses with precious information approximately the effectiveness in their consumer acquisition and retention techniques. By identifying styles amongst users who successfully entire transactions after logging in, agencies can optimize their conversion funnels and enhance average profitability.
3. Personalization and Targeted Marketing:
- Safe Shop login analytics offer the possibility to create customized consumer studies. By understanding consumer preferences, buy history, and interactions with the platform, groups can tailor advertising messages, promotions, and product hints, fostering a greater engaging and relevant experience for customers.
4. Device and Platform Preferences:
- Insights into the devices and structures customers select for Safe Shop login offer treasured facts for optimizing the platform’s compatibility. Businesses can ensure that their internet site and programs are optimized for the most popular devices and working structures, enhancing the overall person enjoy.
5. Login Duration and Session Analysis:
- Analyzing the period of consumer classes after login gives insights into person engagement. Businesses can perceive patterns in person pastime, along with prolonged sessions or brief logins, and use this statistics to enhance the platform’s features, content, and capability to higher align with consumer expectancies.
6. Identifying Abnormal Login Activity:
- Safe Shop login analytics can assist businesses stumble on extraordinary login styles which can suggest ability protection threats or fraudulent activities. Unusual login places, a couple of failed login attempts, or suspicious login instances may be flagged for further research, permitting agencies to proactively deal with safety issues.
7. Geographical Insights:
- Understanding the geographical distribution of Safe Shop logins gives organizations with valuable marketplace insights. This information can inform targeted advertising and marketing efforts, localization techniques, and stock management primarily based on regional call for styles.
Frequently Asked Questions (FAQs)
Safe Shop is a stable authentication and authorization mechanism that performs a vital function in validating user identities in the course of on-line transactions. It ensures the safety of sensitive statistics, protects against unauthorized get right of entry to, and builds accept as true with among agencies and customers.
To access the Safe Shop login web page, go to the official Safe Shop internet site and locate the login phase. This is normally prominently displayed on the homepage or handy through a dedicated login web page.
Safe Shop consists of diverse security capabilities including encryption protocols, -issue authentication (2FA), biometric authentication, account lockout regulations, and steady password practices. These measures collectively enhance the security of the login system.
Related posts:
- Eehhaaa Login: Setting Up Account, Security, Troubleshooting
- CUIMS Login: Instructions, Troubleshooting, Mobile App
- Gitam Web Login: Creating Account, Collaboration, Security
- MDM Login: User Experience, Protection, Secure Access
- MPIGR Login: Guide, Resetting, Troubleshooting, Services
- PPP Login: Documents, Login Guide, Security, Tips
- RGPV Login: Guide, Importance, Troubleshooting, Security
- Ultimatix Login: Guide, Role, Mobile App, Login Issues




















